Quick question for you – you’ve written a couple of columns over the past few years about the area in the outside basement stairwell that has a drain. You recommended in the articles to…


Quick question for you – you’ve written a couple of columns over the past few years about the area in the outside basement stairwell that has a drain. You recommended in the articles to…

While Haryana and Punjab vexed after the CBI court’s conviction of Gurmeet Ram Raheem on Friday, similar incidents erupted in Sriganganagar district of Rajasthan. Agitating in support for Gurmeet Ram Raheem, his supporters set ablaze…
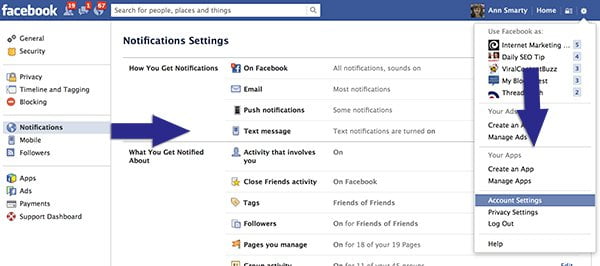
Social media is one of the greatest inventions of the modern world. It allows us to connect with people we lost touch with, keep up with the daily lives of people we care about but…

Social media is one of the greatest inventions of the modern world. It allows us to connect with people we lost touch with, keep up with the daily lives of people we care about but…

A camp for Yazidi refugees, some of whom were about to leave for resettlement in Germany, near Dohuk, Iraq, Jan. 24, 2016. DOHUK, IRAQ: HIGHLIGHTS Rescued women detail horror of being sex slaves for ISIS…

Apple has introduced iCloud Monitoring and Control for HomeKit-enabled Devices at the lately concluded WWDC keynote. The agency additionally announced HomeKit help for a much broader variety ofaccessories, which include security systems and carbon monoxide…

New Delhi: Taking a serious view of non-compliance of DPCO, 2013, the country wide Pharmaceutical Pricing Authority (NPPA) has issued notices to main drug companies for failing to sign up merchandise onon-line database IPDMS and…

The Obama administration plans to renegotiate portions of an international arms control arrangement so it’s simpler to export tools related to hacking and surveillance software, since those technologies are also used to secure computer networks,…